Fixing alerts
Once a secret has been committed to a repository, you should consider the secret compromised. GitHub recommends the following actions for compromised secrets:
- Verify that the secret committed to GitHub is valid.
- Review and update any services that use the old token. For GitHub personal access tokens, delete the compromised token and create a new token. See Managing your personal access tokens.
- Depending on the secret provider, check your security logs for any unauthorized activity.
Closing alerts
Nota:
Secret scanning doesn't automatically close alerts when the corresponding token has been removed from the repository. You must manually close these alerts in the alert list on GitHub.
-
On GitHub, navigate to the main page of the repository.
-
Under the repository name, click Security. If you cannot see the "Security" tab, select the dropdown menu, and then click Security.
-
In the left sidebar, under "Vulnerability alerts", click Secret scanning.
-
Under "Secret scanning", click the alert you want to view.
-
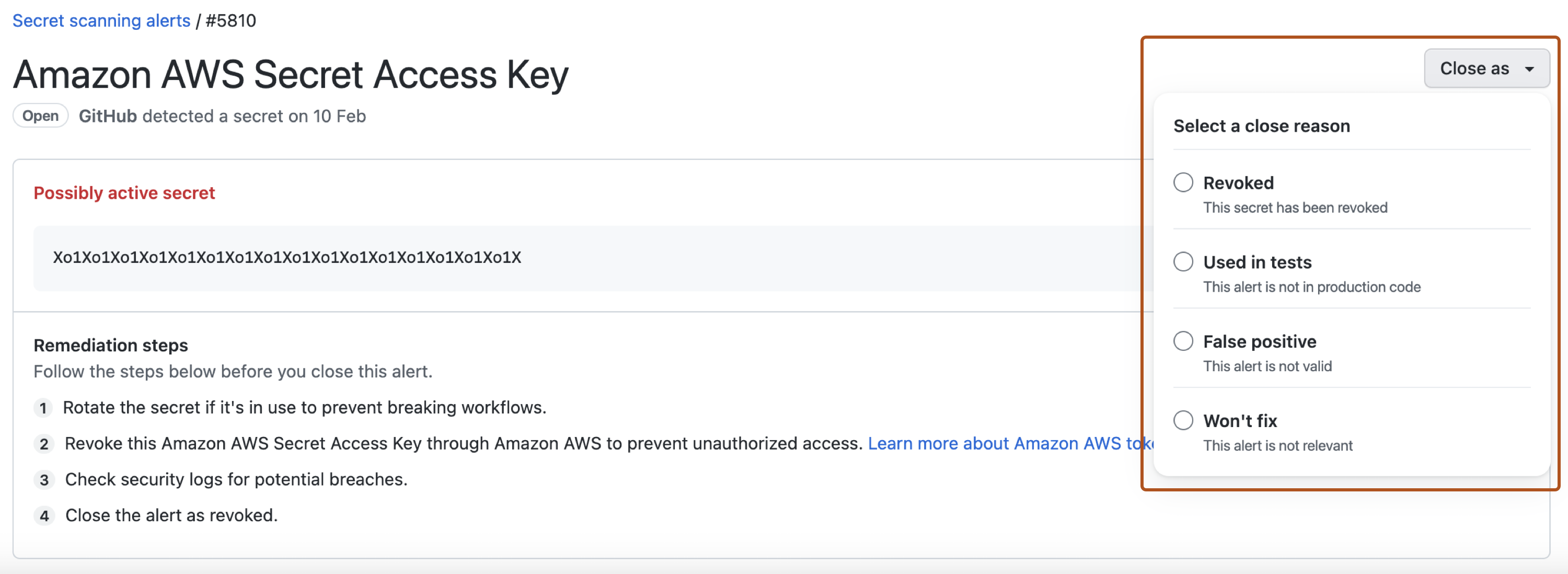
To dismiss an alert, select the "Close as" dropdown menu and click a reason for resolving an alert.
-
Optionally, in the "Comment" field, add a dismissal comment. The dismissal comment will be added to the alert timeline and can be used as justification during auditing and reporting.
-
Click Close alert.