Nota:
Your site administrator must set up Dependabot updates for your GitHub Enterprise Server instance before you can use this feature. For more information, see Enabling Dependabot for your enterprise.
You may not be able to enable or disable Dependabot updates if an enterprise owner has set a policy at the enterprise level. For more information, see Enforcing policies for code security and analysis for your enterprise.
Your repository's Dependabot alerts tab lists all open and closed Dependabot alerts and corresponding Dependabot security updates. You can filter alerts by package, ecosystem, or manifest. You can sort the list of alerts, and you can click into specific alerts for more details. You can also dismiss or reopen alerts, either one by one or by selecting multiple alerts at once. For more information, see About Dependabot alerts.
About updates for vulnerable dependencies in your repository
Each Dependabot alert has a unique numeric identifier and the Dependabot alerts tab lists an alert for every detected vulnerability. Legacy Dependabot alerts grouped vulnerabilities by dependency and generated a single alert per dependency. If you navigate to a legacy Dependabot alert, you will be redirected to a Dependabot alerts tab filtered for that package.
You can filter and sort Dependabot alerts using a variety of filters and sort options available on the user interface. For more information, see Viewing and prioritizing Dependabot alerts below.
You can also audit actions taken in response to Dependabot alerts. For more information, see Auditing security alerts.
Viewing and prioritizing Dependabot alerts
You can view, sort, and filter Dependabot alerts to focus on the alerts that matter most.
By default, alerts are sorted by Most important, which helps you prioritize fixes based on factors such as potential impact, actionability, and relevance. This prioritization is continuously improved and considers signals like CVSS score, dependency scope, and whether vulnerable function calls are detected.
You can view all open and closed Dependabot alerts and corresponding Dependabot security updates in your repository's Dependabot alerts tab.
-
On GitHub, navigate to the main page of the repository.
-
Under the repository name, click Security. If you cannot see the "Security" tab, select the dropdown menu, and then click Security.
-
In the "Vulnerability alerts" sidebar of security overview, click Dependabot. If this option is missing, it means you don't have access to security alerts and need to be given access. For more information, see Managing security and analysis settings for your repository.
-
Optionally, refine the list of alerts:
-
Use the dropdown menus at the top of the list to sort or filter alerts.
-
Type directly in the search bar to filter alerts, including full-text search across alert details and related security advisories.
-
Click a label on an alert to automatically filter the list by that label.
-
To identify alerts that affect development dependencies, filter by the
scope:developmentfilter or look for alerts labeled "Development". This can help you prioritize alerts that affect production dependencies first.
-
-
Click an alert to view its details. Alerts for development-scoped dependencies include a "Development" label in the "Tags" section on the alert details page.
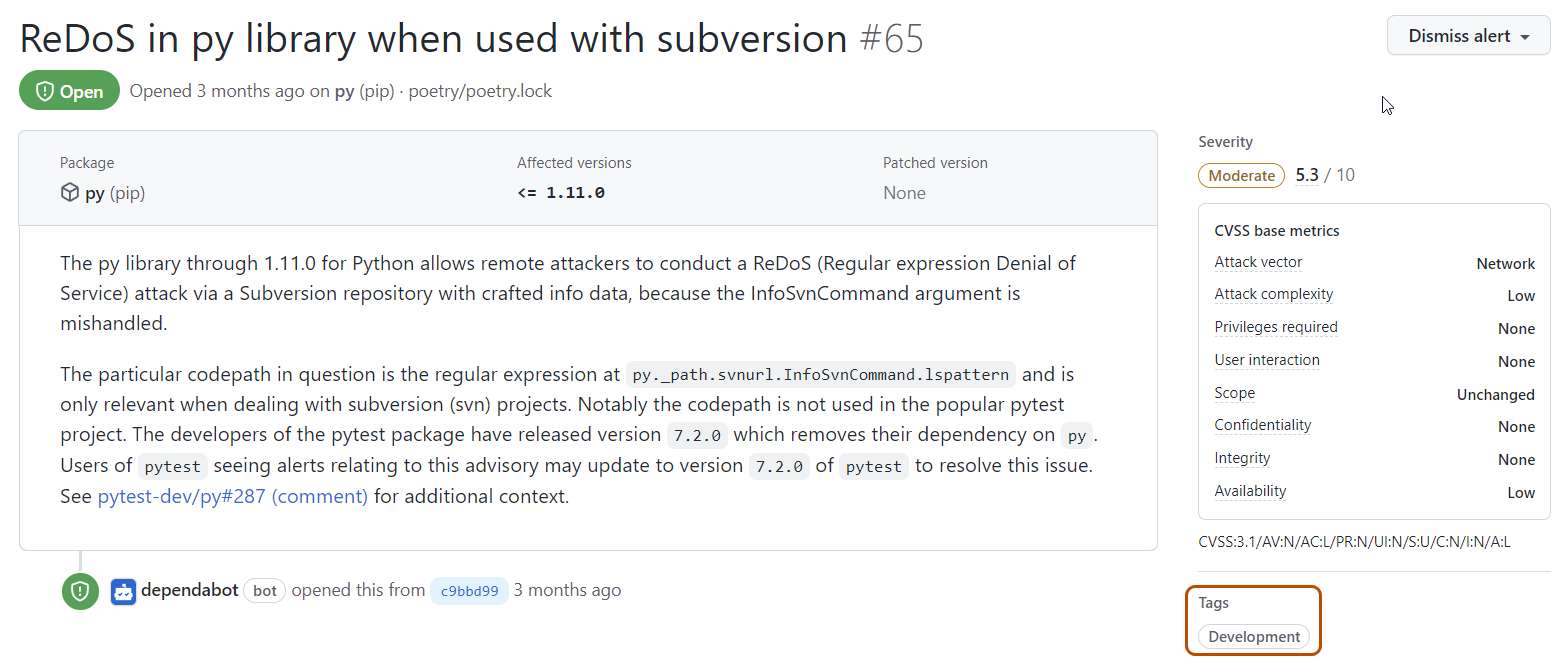
-
Optionally, to suggest an improvement to the related security advisory, on the right-hand side of the alert details page, click Suggest improvements for this advisory on the GitHub Advisory Database. See Editing security advisories in the GitHub Advisory Database.
Tips for prioritizing alerts
- Use the Most important sort order to focus on alerts with the highest potential impact.
- Prioritize alerts that affect production dependencies over development dependencies.
- Use Dependabot auto-triage rules to automatically prioritize or manage alerts. See About Dependabot auto-triage rules.
For more information about supported ecosystems and manifest files for dependency scope, see Supported ecosystems and manifests for dependency scope.
For a complete list of available filters, see Dependabot alert filters.
To retrieve alerts programmatically, see the REST API endpoints for Dependabot alerts.
Reviewing and fixing alerts
You can review the details of a Dependabot alert to understand the vulnerability and how to fix it.
Fixing vulnerable dependencies
-
View the details for an alert. For more information, see Viewing and prioritizing Dependabot alerts (above).
-
If you have Dependabot security updates enabled, there may be a link to a pull request that will fix the dependency. Alternatively, you can click Create Dependabot security update at the top of the alert details page to create a pull request.
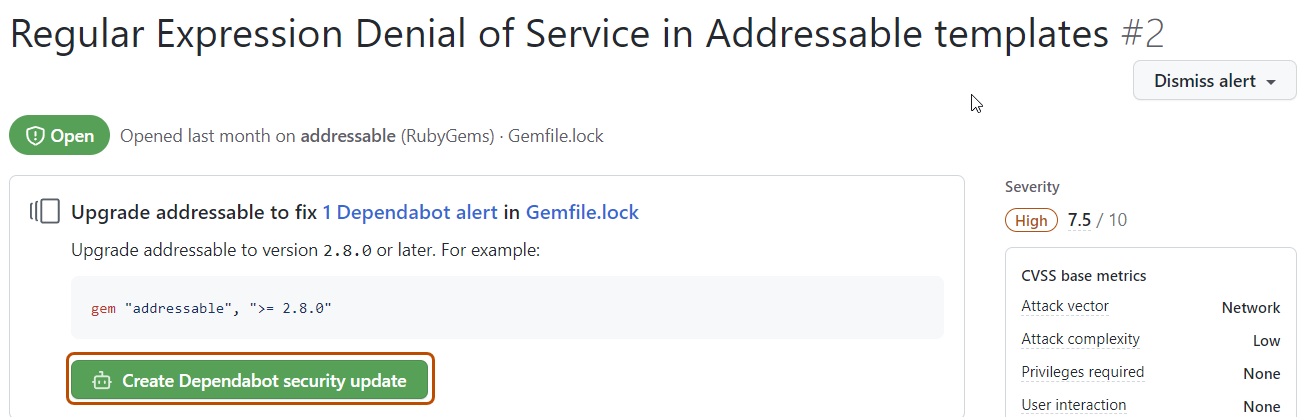
-
Optionally, if you do not use Dependabot security updates, you can use the information on the page to decide which version of the dependency to upgrade to and create a pull request to update the dependency to a secure version.
-
When you're ready to update your dependency and resolve the vulnerability, merge the pull request.
Each pull request raised by Dependabot includes information on commands you can use to control Dependabot. For more information, see Managing pull requests for dependency updates.
Dismissing Dependabot alerts
Nota:
You can only dismiss open alerts.
If you schedule extensive work to upgrade a dependency, or decide that an alert does not need to be fixed, you can dismiss the alert. Dismissing alerts that you have already assessed makes it easier to triage new alerts as they appear.
-
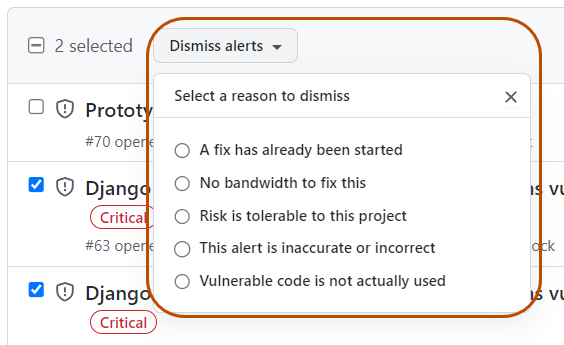
Select the "Dismiss" dropdown, and click a reason for dismissing the alert. Unfixed dismissed alerts can be reopened later.
-
Optionally, add a dismissal comment. The dismissal comment will be added to the alert timeline and can be used as justification during auditing and reporting. You can retrieve or set a comment by using the GraphQL API. The comment is contained in the
dismissCommentfield. For more information, see Objects in the GraphQL API documentation.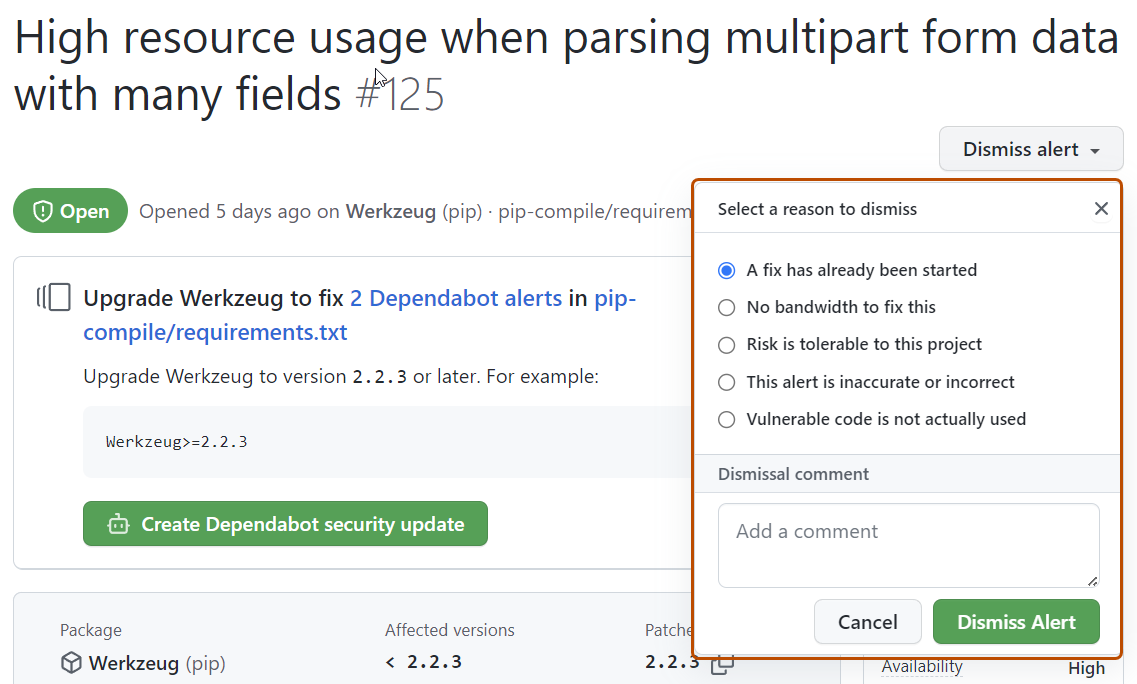
-
Click Dismiss alert.
Dismissing multiple alerts at once
- View the open Dependabot alerts.
- Optionally, filter the list of alerts by selecting a dropdown menu, then clicking the filter that you would like to apply. You can also type filters into the search bar.
- To the left of each alert title, select the alerts that you want to dismiss.
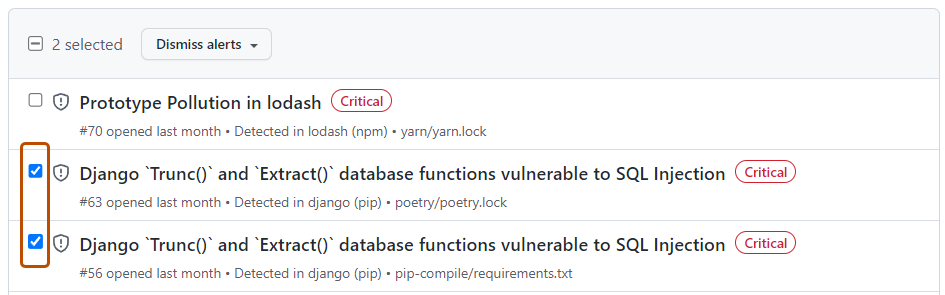
- Optionally, at the top of the list of alerts, select all alerts on the page.
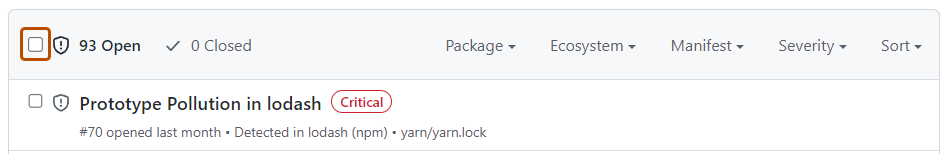
- Select the "Dismiss alerts" dropdown, and click a reason for dismissing the alerts.
Viewing and updating closed alerts
You can view all open alerts, and you can reopen alerts that have been previously dismissed. Closed alerts that have already been fixed cannot be reopened.
-
On GitHub, navigate to the main page of the repository.
-
Under the repository name, click Security. If you cannot see the "Security" tab, select the dropdown menu, and then click Security.

-
In the "Vulnerability alerts" sidebar of security overview, click Dependabot. If this option is missing, it means you don't have access to security alerts and need to be given access. For more information, see Managing security and analysis settings for your repository.

-
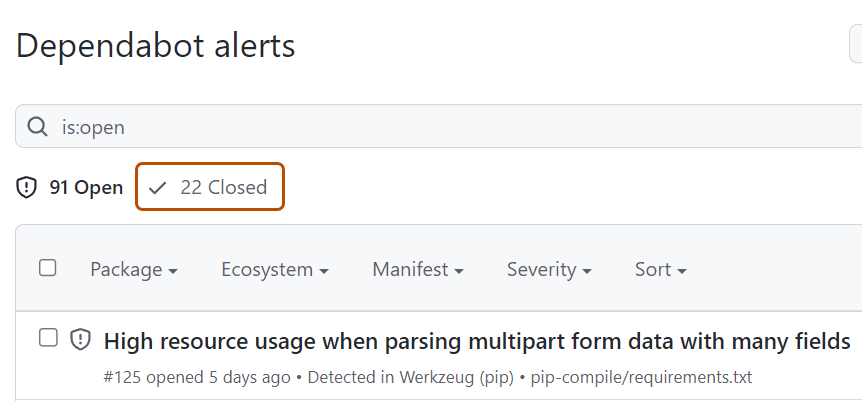
To just view closed alerts, click Closed.
-
Click the alert that you would like to view or update.
-
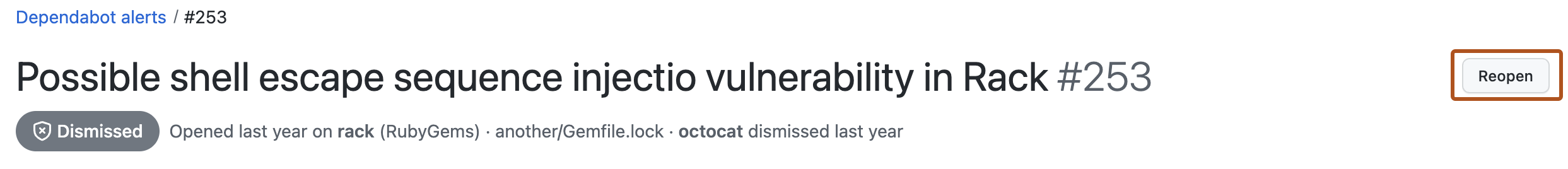
Optionally, if the alert was dismissed and you wish to reopen it, click Reopen. Alerts that have already been fixed cannot be reopened.
Reopening multiple alerts at once
- View the closed Dependabot alerts.
- To the left of each alert title, select the alerts that you want to reopen by clicking the checkbox adjacent to each alert.
- Optionally, at the top of the list of alerts, select all closed alerts on the page.
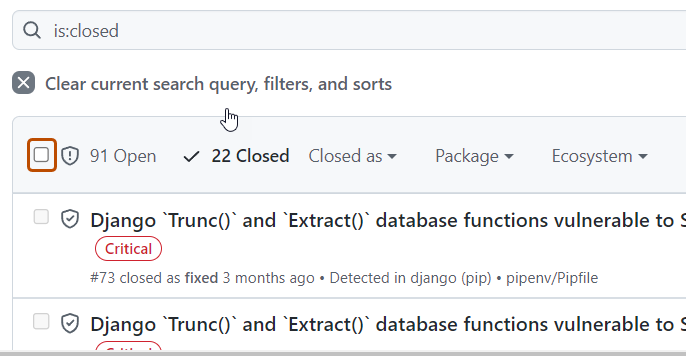
- Click Reopen to reopen the alerts. Alerts that have already been fixed cannot be reopened.
Reviewing the audit logs for Dependabot alerts
When a member of your organization or enterprise performs an action related to Dependabot alerts, you can review the actions in the audit log. For more information about accessing the log, see Reviewing the audit log for your organization and Accessing the audit log for your enterprise.
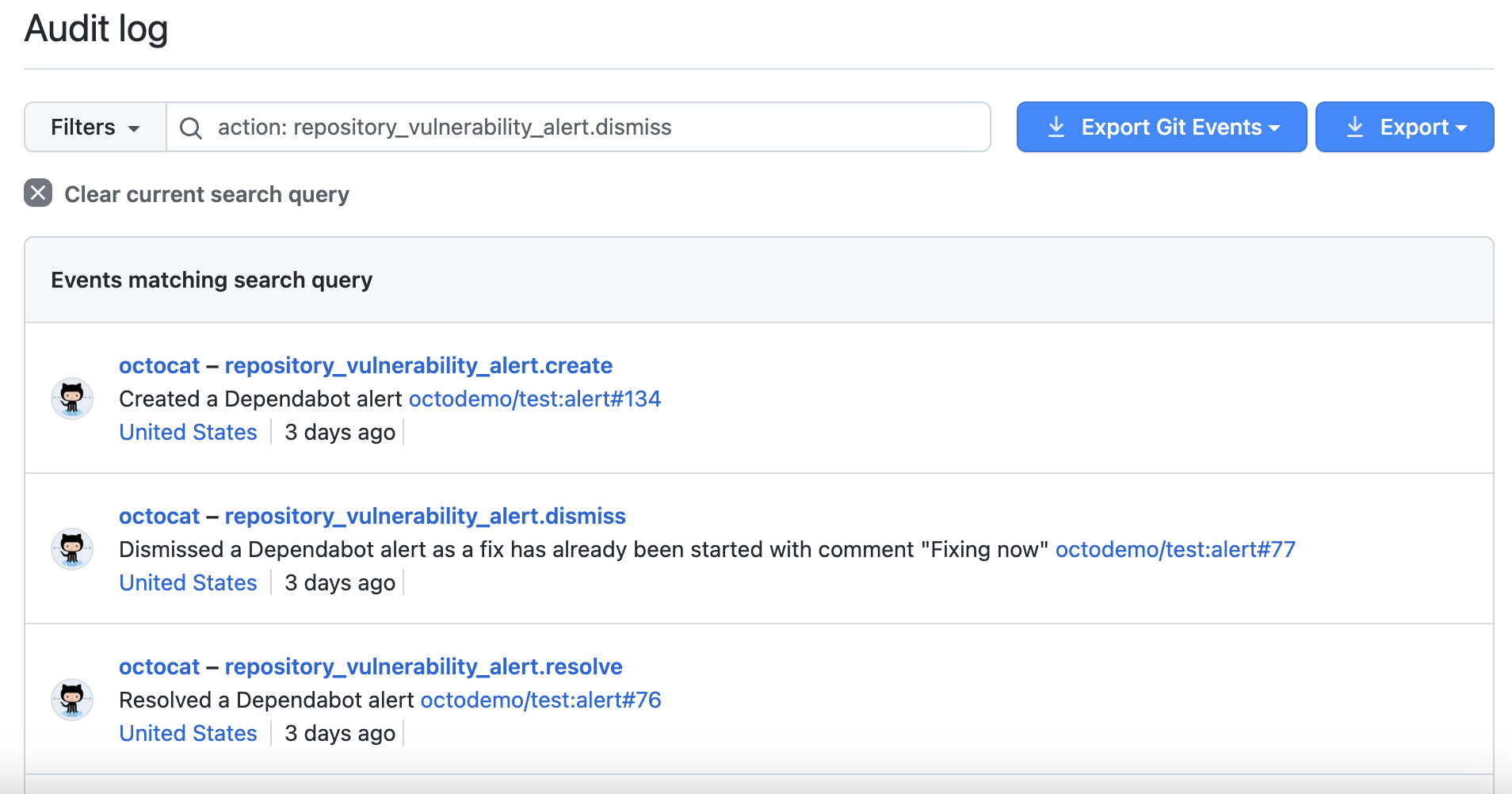
Events in your audit log for Dependabot alerts include details such as who performed the action, what the action was, and when the action was performed. The event also includes a link to the alert itself. When a member of your organization dismisses an alert, the event displays the dismissal reason and comment. For information on the Dependabot alerts actions, see the repository_vulnerability_alert category in Audit log events for your organization and Audit log events for your enterprise.