Übersicht über OpenID Connect (OIDC)
GitHub Actions-Workflows sind häufig für den Zugriff auf einen Cloudanbieter (z. B. AWS, Azure, GCP, HashiCorp Vault und andere) ausgelegt, um Software bereitzustellen oder die Dienste der jeweiligen Cloud zu verwenden. Bevor der Workflow auf diese Ressourcen zugreifen kann, werden dem Cloudanbieter Anmeldeinformationen, z. B. ein Kennwort oder ein Token, bereitgestellt. Diese Anmeldeinformationen werden in der Regel als Geheimnis in GitHub gespeichert, und der Workflow stellt dieses Geheimnis bei jeder Ausführung für den Cloudanbieter bereit.
Die Verwendung von hart codierten Geheimnissen erfordert jedoch, dass du Anmeldeinformationen im Cloudanbieter erstellst und dann als Geheimnis in GitHub duplizierst.
Nachdem du eine vertrauenswürdige Verbindung mit einem Cloudanbieter hergestellt hast, der OIDC unterstützt, kannst du deinen Workflow so konfigurieren, dass ein kurzlebiges Zugriffstoken direkt vom Cloudanbieter angefordert wird.
Vorteile der Verwendung von OIDC
Wenn du deine Workflows für die Verwendung von OIDC-Token aktualisierst, kannst du die folgenden bewährten Sicherheitspraktiken übernehmen:
- Keine Cloudgeheimnisse: Du musst deine Cloudanmeldeinformationen nicht als langlebige GitHub-Geheimnisse duplizieren. Stattdessen kannst du die OIDC-Vertrauensstellung auf deinem Cloudanbieter konfigurieren und dann deine Workflows aktualisieren, um ein kurzlebiges Zugriffstoken vom Cloudanbieter über OIDC anzufordern.
- Authentifizierungs- und Autorisierungsverwaltung: Du hast genauere Kontrolle darüber, wie Workflows Anmeldeinformationen verwenden können, indem du die Authentifizierungs- (authN) und Autorisierungstools (authZ) deines Cloudanbieters verwendest, um den Zugriff auf Cloudressourcen zu steuern.
- Rotierende Anmeldeinformationen: Mit OIDC stellt dein Cloudanbieter ein kurzlebiges Zugriffstoken aus, das nur für einen einzelnen Auftrag gültig ist und dann automatisch abläuft.
Übersicht über die Integration von OIDC mit GitHub Actions
Im folgenden Diagramm siehst du, wie der OIDC-Anbieter von GitHub mit deinen Workflows und dem Cloudanbieter integriert ist:
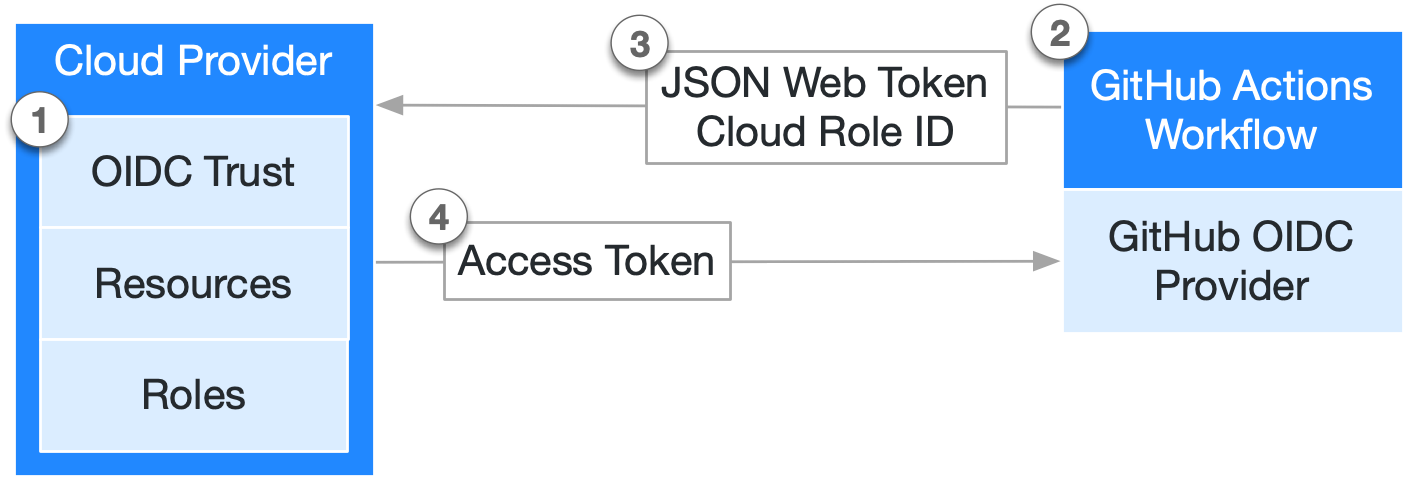
- Du erstellst in deinem Cloudanbieter eine OIDC-Vertrauensstellung, die es bestimmten GitHub-Workflows ermöglicht, Cloudzugriffstoken im Auftrag einer definierten Cloudrolle anzufordern.
- Jedes Mal, wenn dein Auftrag ausgeführt wird, generiert der OIDC-Anbieter von GitHub automatisch ein OIDC-Token. Dieses Token enthält mehrere Ansprüche zum Einrichten einer sicherheitsfesten und überprüften Identität über den spezifischen Workflow, der versucht, sich zu authentifizieren.
- Ein Schritt oder eine Aktion innerhalb des Workflowauftrags kann vom OIDC-Anbieter von GitHub ein Token anfordern, das anschließend dem Cloudanbieter als Nachweis für die Workflowidentität übermittelt werden kann.
- Nachdem der Cloudanbieter die im Token dargestellten Ansprüche erfolgreich überprüft hat, stellt er ein kurzlebiges Cloudzugriffstoken bereit, das nur für die Dauer des Auftrags verfügbar ist.
Grundlegendes zum OIDC-Token
Jeder Auftrag fordert ein OIDC-Token vom OIDC-Anbieter von GitHub an, der mit einem automatisch generierten JSON-Webtoken (JWT) reagiert, das für jeden Workflowauftrag, in dem es generiert wird, eindeutig ist. Wenn der Auftrag ausgeführt wird, wird das OIDC-Token für den Cloudanbieter bereitgestellt. Zur Überprüfung des Tokens ermittelt der Cloudanbieter, ob der Antragsteller des OIDC-Tokens und andere Ansprüche mit den Bedingungen übereinstimmen, die für die OIDC-Vertrauensdefinition der Cloudrolle vorkonfiguriert wurden.
Im folgenden Beispiel verwendet das OIDC-Token einen Antragsteller (sub), der auf eine Auftragsumgebung namens prod im Repository octo-org/octo-repo verweist.
{
"typ": "JWT",
"alg": "RS256",
"x5t": "example-thumbprint",
"kid": "example-key-id"
}
{
"jti": "example-id",
"sub": "repo:octo-org/octo-repo:environment:prod",
"environment": "prod",
"aud": "https://HOSTNAME/octo-org",
"ref": "refs/heads/main",
"sha": "example-sha",
"repository": "octo-org/octo-repo",
"repository_owner": "octo-org",
"actor_id": "12",
"repository_visibility": "private",
"repository_id": "74",
"repository_owner_id": "65",
"run_id": "example-run-id",
"run_number": "10",
"run_attempt": "2",
"runner_environment": "github-hosted",
"actor": "octocat",
"workflow": "example-workflow",
"head_ref": "",
"base_ref": "",
"event_name": "workflow_dispatch",
"enterprise": "avocado-corp",
"enterprise_id": "2",
"ref_type": "branch",
"job_workflow_ref": "octo-org/octo-automation/.github/workflows/oidc.yml@refs/heads/main",
"iss": "https://HOSTNAME/_services/token",
"nbf": 1632492967,
"exp": 1632493867,
"iat": 1632493567
}
Authentifizieren benutzerdefinierter Aktionen mit OIDC
Benutzerdefinierte Aktionen verwenden für die Authentifizierung mit OIDC die getIDToken()-Methode aus dem Toolkit für Aktionen oder einen curl-Befehl.
Weitere Informationen finden Sie unter OpenID Connect-Referenz.
Aktualisieren deiner Workflows für OIDC
GitHub Actions-Workflows können zur Authentifizierung bei Cloudanbietern OIDC-Token anstelle von Geheimnissen verwenden. Viele beliebte Cloudanbieter bieten offizielle Anmeldeaktionen, die den Verwendungsprozess von OIDC in Workflows vereinfachen. Weitere Informationen zum Aktualisieren deiner Workflows bei bestimmten Cloudanbietern findest du unter Sicherheitshärtung deiner Bereitstellungen.
Nächste Schritte
Weitere Informationen zum Konfigurieren von OIDC findest du unter Sicherheitshärtung deiner Bereitstellungen.
Referenzinformationen zu OIDC findest du unter OpenID Connect-Referenz.