Arbeiten mit dem Actions Runner Controller (ARC)
Dieser Artikel enthält Schrittanleitungen zum Einrichten von ARC auf einem Kubernetes-Cluster und zum Konfigurieren von Dependabot für die Ausführung auf selbstgehosteten Aktionsrunnern. Der Artikel enthält Folgendes:
- Er enthält eine Übersicht über die ARC- und Dependabot-Integration.
- Er enthält detaillierte Installations- und Konfigurationsschritte mithilfe von Helm-Skripts.
Was ist ARC?
Der Actions Runner Controller ist ein Kubernetes-Controller, der selbstgehostete GitHub Actions als Kubernetes-Pods verwaltet. Er ermöglicht es, Runner basierend auf deinen Workflows dynamisch zu skalieren und zu koordinieren und eine bessere Ressourcenauslastung und Integration in Kubernetes-Umgebungen zu ermöglichen. Weitere Informationen findest du unter Actions Runner Controller.
Dependabot in ARC
Du kannst Dependabot auf selbstgehosteten GitHub Actions-Runnern ausführen, die innerhalb eines Kubernetes-Clusters über ARC verwaltet werden. Dies ermöglicht die automatische Skalierung, Workloadisolation und eine bessere Ressourcenverwaltung für Dependabot-Aufträge, wodurch sichergestellt wird, dass Abhängigkeitsupdates effizient in der kontrollierten Infrastruktur einer Organisation ausgeführt und gleichzeitig nahtlos in GitHub Actions integriert werden können.
Einrichten von ARC für Dependabot in der lokalen Umgebung
Voraussetzungen
- Ein Kubernetes-Cluster
- Für eine verwaltete Cloudumgebung kannst du Azure Kubernetes Service (AKS) verwenden.
- Für ein lokales Setup kannst du minikube verwenden.
- Helm
- Ein Paket-Manager für Kubernetes.
Einrichten von ARC
-
Installiere ARC. Weitere Informationen finden Sie unter Schnellstart für Actions Runner Controller.
-
Erstelle ein Arbeitsverzeichnis für das ARC-Setup und eine Shell-Skriptdatei (z. B.
helm_install_arc.sh), um die neueste ARC-Version zu installieren.Bash mkdir ARC touch helm_install_arc.sh chmod 755 helm_install_arc.shmkdir ARC touch helm_install_arc.sh chmod 755 helm_install_arc.sh -
Bearbeite
helm_install_arc.shmit diesem Bash-Skript zum Installieren von ARC.Text NAMESPACE="arc-systems" helm install arc \ --namespace "${NAMESPACE}" \ --create-namespace \ oci://ghcr.io/actions/actions-runner-controller-charts/gha-runner-scale-set-controllerNAMESPACE="arc-systems" helm install arc \ --namespace "${NAMESPACE}" \ --create-namespace \ oci://ghcr.io/actions/actions-runner-controller-charts/gha-runner-scale-set-controller -
Führe die Skriptdatei
helm_install_arc.shaus../helm_install_arc.sh -
Jetzt musst du die Skalierungsgruppe für den Runner konfigurieren. Beginnen wir damit, eine Datei mit dem folgenden Bash-Skript zu erstellen und zu bearbeiten.
Bash touch arc-runner-set.sh chmod 755 arc-runner-set.sh
touch arc-runner-set.sh chmod 755 arc-runner-set.shText INSTALLATION_NAME="dependabot" NAMESPACE="arc-runners" GITHUB_CONFIG_URL=REPO_URL GITHUB_PAT=PAT helm install "${INSTALLATION_NAME}" \ --namespace "${NAMESPACE}" \ --create-namespace \ --set githubConfigUrl="${GITHUB_CONFIG_URL}" \ --set githubConfigSecret.github_token="${GITHUB_PAT}" \ --set containerMode.type="dind" \ oci://ghcr.io/actions/actions-runner-controller-charts/gha-runner-scale-setINSTALLATION_NAME="dependabot" NAMESPACE="arc-runners" GITHUB_CONFIG_URL=REPO_URL GITHUB_PAT=PAT helm install "${INSTALLATION_NAME}" \ --namespace "${NAMESPACE}" \ --create-namespace \ --set githubConfigUrl="${GITHUB_CONFIG_URL}" \ --set githubConfigSecret.github_token="${GITHUB_PAT}" \ --set containerMode.type="dind" \ oci://ghcr.io/actions/actions-runner-controller-charts/gha-runner-scale-set -
Führe die Skriptdatei
arc-runner-set.shaus.Bash ./arc-runner-set.sh
./arc-runner-set.sh
Hinweis
- Der Installationsname der Skalierungsgruppe für den Runner muss
dependabotsein, um den Dependabot-Auftrag auf den Runner auszurichten. - Die
containerMode.type="dind"-Konfiguration ist erforderlich, damit der Runner eine Verbindung mit dem Docker-Daemon herstellen kann. - Wenn ein Runner auf Organisationsebene oder Unternehmensebene erstellt wird, sollten die entsprechenden Bereiche dem Personal Access Token (PAT) angegeben werden.
- Es kann ein personal access token (classic) (PAT) erstellt werden. Das Token sollte über die folgenden Bereiche verfügen, je nachdem, ob du ein Repository, eine Organisation oder eine Skalierungsgruppe für den Runner auf Unternehmensebene erstellst.
- Repositoryebene: repo
- Organisationsebene: admin:org
- Unternehmensebene: admin:enterprise
Informationen zum Erstellen eines personal access token (classic) findest du unter Verwalten deiner persönlichen Zugriffstoken.
Hinzufügen von Runnergruppen
Mit Runnergruppen kann gesteuert werden, welche Organisationen oder Repositorys Zugriff auf deine Runner-Skalierungsgruppen erhalten sollen. Damit du einer Runnergruppe eine Runner-Skalierungsgruppe hinzufügen kannst, musst du bereits eine Runnergruppe erstellt haben.
Informationen zum Erstellen von Runnergruppen findest du unter Verwalten des Zugriffs auf selbstgehostete Runner mithilfe von Gruppen.
Vergiss nicht, die folgende Einstellung zur Konfiguration der Skalierungsgruppe für Runner im Helm-Diagramm hinzuzufügen.
--set runnerGroup="<Runner group name>" \
--set runnerGroup="<Runner group name>" \
Überprüfen der Installation
-
Überprüfe deine Installation.
Bash helm list -A
helm list -AAusgabe:
➜ ARC git:(master) ✗ helm list -A NAME NAMESPACE REVISION UPDATED STATUS CHART APP VERSION arc arc-systems 1 2025-04-11 14:41:53.70893 -0500 CDT deployed gha-runner-scale-set-controller-0.11.0 0.11.0 arc-runner-set arc-runners 1 2025-04-11 15:08:12.58119 -0500 CDT deployed gha-runner-scale-set-0.11.0 0.11.0 dependabot arc-runners 1 2025-04-16 21:53:40.080772 -0500 CDT deployed gha-runner-scale-set-0.11.0 -
Überprüfe den Manager-Pod mit diesem Befehl.
Bash kubectl get pods -n arc-systems
kubectl get pods -n arc-systemsAusgabe:
➜ ARC git:(master) ✗ kubectl get pods -n arc-systems NAME READY STATUS RESTARTS AGE arc-gha-rs-controller-57c67d4c7-zjmw2 1/1 Running 8 (36h ago) 6d9h arc-runner-set-754b578d-listener 1/1 Running 0 11h dependabot-754b578d-listener 1/1 Running 0 14h
Einrichten von Dependabot
-
Navigieren Sie auf GitHub zur Hauptseite des Repositorys.
-
Klicke unter dem Repositorynamen auf Settings. Wenn die Registerkarte „Einstellungen“ nicht angezeigt wird, wähle im Dropdownmenü die Option Einstellungen aus.
-
Klicke im Abschnitt „Security“ der Randleiste auf Advanced Security.
-
Scrolle unter „Dependabot“ zu „Dependabot on Action Runners“, und wähle Enable für „Dependabot on self-hosted runners“ aus.
Auslösen einer Dependabot-Ausführung
Nachdem du ARC eingerichtet hast, kannst du eine Dependabot-Ausführung starten.
-
Navigieren Sie auf GitHub zur Hauptseite des Repositorys.
-
Klicke unter dem Repositorynamen auf die Registerkarte Insights.
-
Klicke auf der linken Randleiste auf Abhängigkeitsdiagramm.
-
Klicke unter „Abhängigkeitsdiagramm“ auf Dependabot .
-
Klicke rechts neben dem Namen der relevanten Manifestdatei auf Recent update jobs.
-
Wenn keine kürzlichen Aktualisierungsaufträge für die Manifestdatei vorhanden sind, klicke auf Check for updates, um einen Dependabot-Versionsupdateauftrag erneut auszuführen und nach neuen Updates für Abhängigkeiten für dieses Ökosystem zu suchen.
Anzeigen der generierten ARC-Runner
Du kannst die ARC-Runner anzeigen, die für den Dependabot-Auftrag erstellt wurden.
-
Navigieren Sie auf GitHub zur Hauptseite des Repositorys.
-
Klicke unter dem Repositorynamen auf Actions.
-
Klicke auf der linken Randleiste auf Runners.
-
Klicke unter „Runners“ auf Self-hosted runners, um eine Lister aller im Repository verfügbaren Runner anzuzeigen. Du siehst den kurzlebigen Dependabot-Runner, der erstellt wurde.
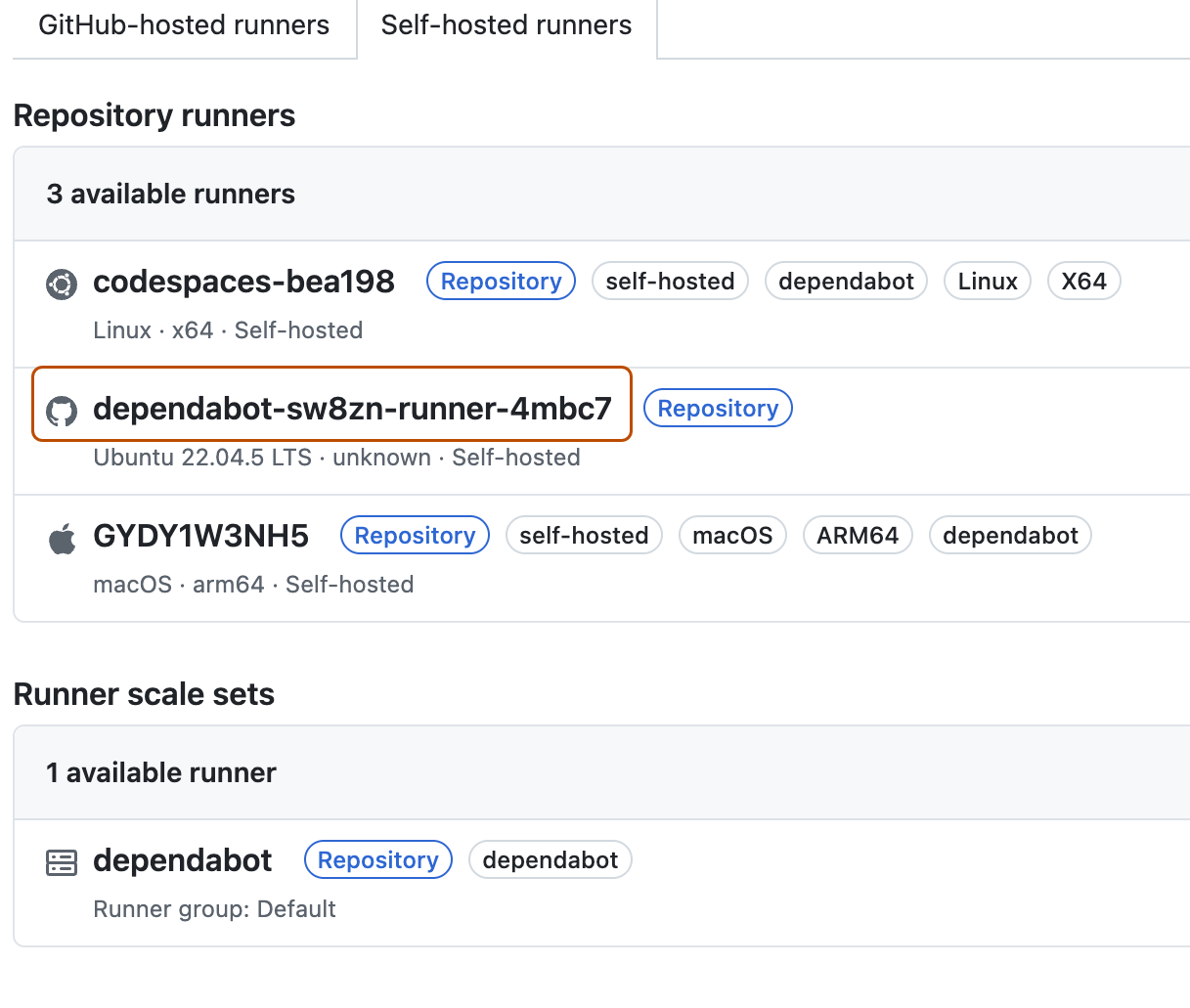
Du kannst diesen Dependabot-Runner-Pod, der in deinem Kubernetes-Cluster erstellt wurde, auch über das Terminal anzeigen, indem du diesen Befehl ausführst.
Text ➜ ARC git:(master) ✗ kubectl get pods -n arc-runners NAME READY STATUS RESTARTS AGE dependabot-sw8zn-runner-4mbc7 2/2 Running 0 46s➜ ARC git:(master) ✗ kubectl get pods -n arc-runners NAME READY STATUS RESTARTS AGE dependabot-sw8zn-runner-4mbc7 2/2 Running 0 46s
Darüber hinaus kannst du Folgendes überprüfen:
-
Die Protokolle, durch Überprüfen des Runner- und Computernamens Weitere Informationen findest du unter Anzeigen von Dependabot-Auftragsprotokollen.
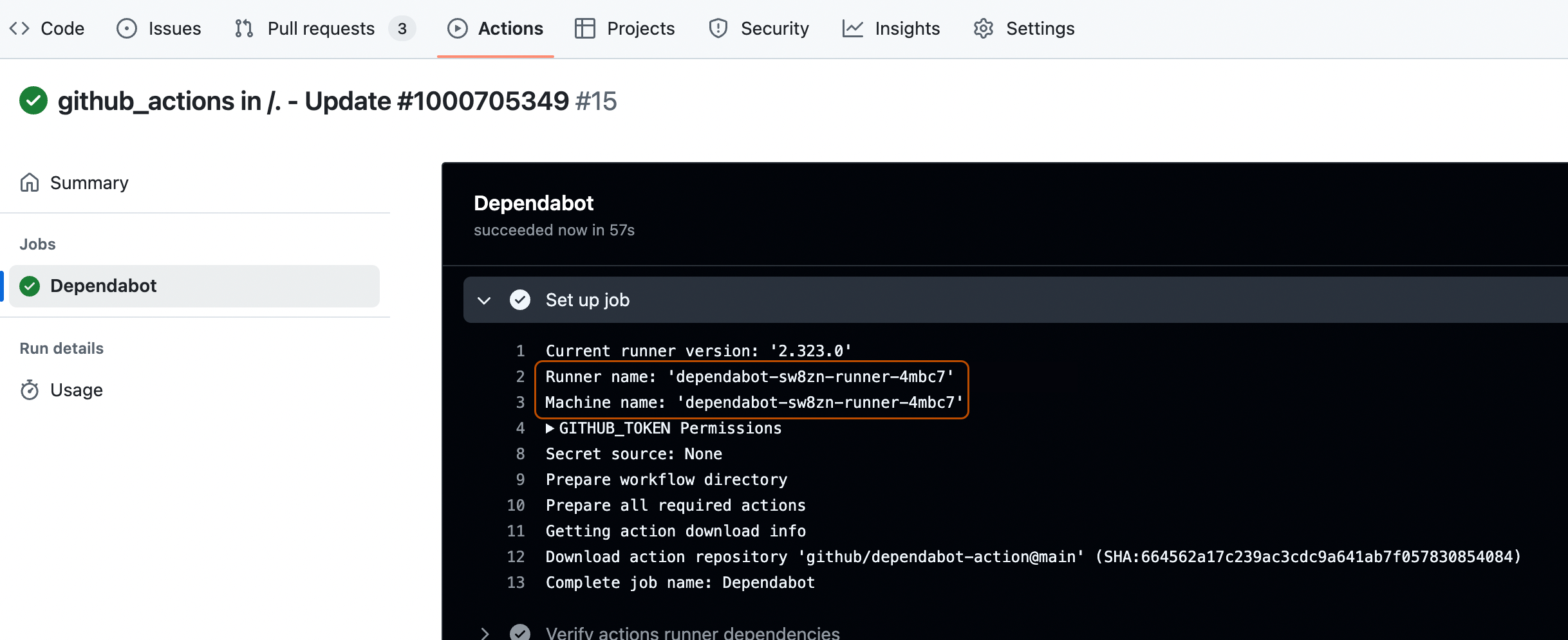
-
Die Pull Requests für Versionsupdates, die durch den Dependabot-Auftrag erstellt wurden (auf der Registerkarte Pull requests des Repositorys)