About policies for using security features in your enterprise
You can enforce policies to manage the use of security features within organizations owned by your enterprise. You can allow or disallow people with admin access to a repository to enable or disable the security and analysis features.
Additionally, you can enforce policies for the use of GitHub Secret Protection, GitHub Code Security and GitHub Code Quality (public preview), or GitHub Advanced Security in your enterprise's organizations and repositories.
Enforcing a policy for the availability of Advanced Security in your enterprise's organizations
You are billed for GitHub Secret Protection, GitHub Code Security, and GitHub Advanced Security products on a per-committer basis. See GitHub Advanced Security license billing.
You can enforce a policy that controls whether repository administrators are allowed to enable features for Advanced Security in an organization's repositories. You can configure a policy for all organizations owned by your enterprise account, or for individual organizations that you choose.
Disallowing GitHub Secret Protection, GitHub Code Security and GitHub Code Quality (public preview), or GitHub Advanced Security for an organization prevents repository administrators from enabling these features for additional repositories, but does not disable the features for repositories where the features are already enabled.
Note
This policy only impacts repository administrators, specifically. Organization owners and security managers can always enable security features, regardless of how you set this policy. For more information, see Roles in an organization.
-
In the top-right corner of GitHub, click your profile picture.
-
Depending on your environment, click Enterprise, or click Enterprises then click the enterprise you want to view.
-
At the top of the page, click Policies.
-
Under "Policies", click Advanced Security.
-
On the "Policies" tab of the "Advanced Security" page, select the dropdown menu, then click a policy for the organizations owned by your enterprise.
-
Optionally, if you chose Allow for selected organizations, to the right of an organization, select the dropdown menu to define which Advanced Security products are available to the organization.
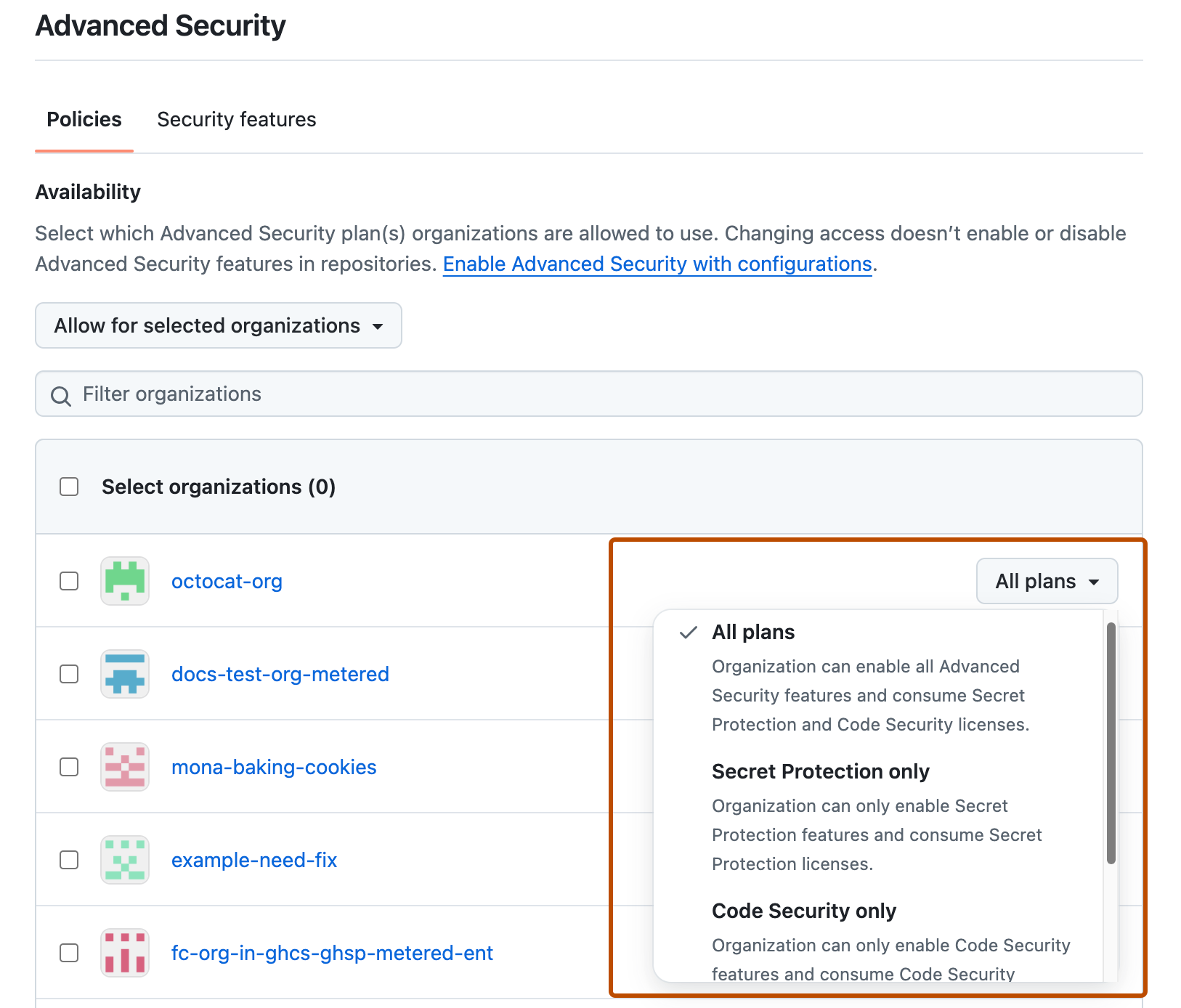
Note
If GitHub Actions is not available for an organization, code scanning and GitHub Code Quality will be unable to run even if they are made available with this policy. See Enforcing policies for GitHub Actions in your enterprise.
Enforcing a policy for visibility of dependency insights
Dependency insights show all open source projects that repositories within your enterprise's organizations depend on. Dependency insights include aggregated information about security advisories and licenses. For more information, see Viewing insights for dependencies in your organization.
Across all organizations owned by your enterprise, you can control whether organization members can view dependency insights. You can also allow owners to administer the setting on the organization level. For more information, see Changing the visibility of your organization's dependency insights.
-
In the top-right corner of GitHub, click your profile picture.
-
Depending on your environment, click Enterprise, or click Enterprises then click the enterprise you want to view.
-
At the top of the page, click Policies.
-
Under "Policies", click Advanced Security.
-
In the "Policies" section, under "Dependency insights", review the information about changing the setting.
-
Optionally, to view the current configuration for all organizations in the enterprise account before you change the setting, click View your organizations' current configurations.
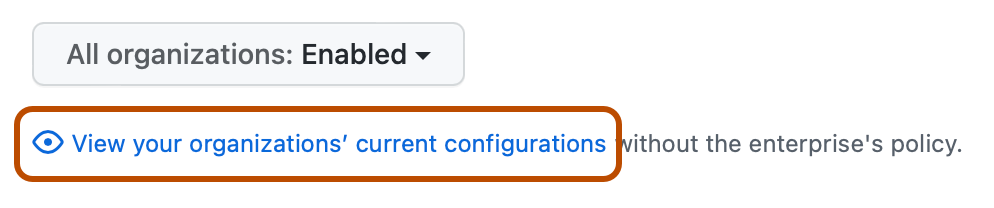
-
Under "Dependency insights", select the dropdown menu and click a policy.
Enforcing a policy to manage the use of Dependabot alerts in your enterprise
Across all organizations owned by your enterprise, you can allow members with admin permissions for repositories to enable or disable Dependabot alerts and change Dependabot alerts settings.
Note
This policy only impacts repository administrators, specifically. Organization owners and security managers can always enable security features, regardless of how you set this policy. For more information, see Roles in an organization.
- In the top-right corner of GitHub, click your profile picture.
- Depending on your environment, click Enterprise, or click Enterprises then click the enterprise you want to view.
- At the top of the page, click Policies.
- Under "Policies", click Advanced Security.
- In the "Policies" section, under "Enable or disable Dependabot alerts by repository admins", use the dropdown menu to choose a policy.
Enforcing a policy to manage the use of Advanced Security features in your enterprise's repositories
Across all of your enterprise's organizations, you can allow or disallow people with admin access to repositories to manage the use of Advanced Security features in the repositories.
-
In the top-right corner of GitHub, click your profile picture.
-
Depending on your environment, click Enterprise, or click Enterprises then click the enterprise you want to view.
-
At the top of the page, click Policies.
-
Under "Policies", click Advanced Security.
-
In the "Policies" section, under "Repository administrators can enable or disable
PRODUCT", use the dropdown menu to define whether repository administrators can change the enablement of GitHub Secret Protection, GitHub Code Security and GitHub Code Quality (public preview), or GitHub Advanced Security.
Enforcing a policy to manage the use of AI detection for secret scanning in your enterprise's repositories
Across all of your enterprise's organizations, you can allow or disallow people with admin access to repositories to manage and configure AI detection in secret scanning for the repositories. This policy only takes effect if repository administrators are also allowed to change enablement of Secret Protection (controlled by the "Repository administrators can enable or disable Secret Protection" policy).
- In the top-right corner of GitHub, click your profile picture.
- Depending on your environment, click Enterprise, or click Enterprises then click the enterprise you want to view.
- At the top of the page, click Policies.
- Under "Policies", click Advanced Security.
- In the "Policies" section, under "AI detection in secret scanning", select the dropdown menu and click a policy.
Enforcing a policy to manage the use of Copilot Autofix in your enterprise's repositories
Across all of your enterprise's organizations, you can allow or disallow people with admin access to repositories to manage where Copilot Autofix is enabled for Code Security results. GitHub Code Security must be enabled for the organization for this policy to take effect.
- In the top-right corner of GitHub, click your profile picture.
- Depending on your environment, click Enterprise, or click Enterprises then click the enterprise you want to view.
- At the top of the page, click Policies.
- Under "Policies", click Advanced Security.
- In the "Policies" section, under "Copilot Autofix", select the dropdown menu and click a policy.
Note
This policy controls the use of Copilot Autofix on results found by code scanning security queries only. Copilot Autofix is an integral part of GitHub Code Quality and cannot be disabled for that feature.