Username conflicts
GitHub normalizes the SCIM userName attribute value that is sent by an identity provider (IdP) in a SCIM API call to create each person's username on GitHub. If multiple accounts are normalized into the same GitHub username, a username conflict occurs, and only the first user account is created. For more information, see Username considerations for external authentication.
Accessing your enterprise when SSO is not available
When a configuration error or an issue with your identity provider IdP prevents you from using SSO, you can use a site admin with access to the Management Console to update your settings, or disable SAML temporarily. For more information, see Administering your instance from the web UI.
SCIM provisioning errors
Microsoft Entra ID (previously known as Azure AD) will retry SCIM provisioning attempts automatically during the next Entra ID sync cycle. The default SCIM provisioning interval for Entra ID is 40 minutes. For more information about this retry behavior, see the Microsoft documentation or contact Microsoft support if you need additional assistance.
Okta will retry failed SCIM provisioning attempts with manual Okta admin intervention. For more information about how an Okta admin can retry a failed task for a specific application, see the Okta documentation or contact Okta support.
In your instance where SCIM is generally functioning properly, individual user SCIM provisioning attempts sometimes fail. Users will be unable to sign in until their account is provisioned to GitHub. These individual SCIM user provisioning failures result in an HTTP 400 range status code and are typically caused by issues with username normalization or username conflicts, where another user with the same normalized username already exists in the enterprise. See Username considerations for external authentication.
SAML authentication errors
If users are experiencing errors when attempting to authenticate with SAML, see Troubleshooting SAML authentication.
SAML and SCIM data mapping errors
If you use SAML with SCIM on your GitHub Enterprise Server instance, and a user's SAML data does not match to an existing SCIM provisioned identity, GitHub will return an error.
For Entra ID, the error will look like:
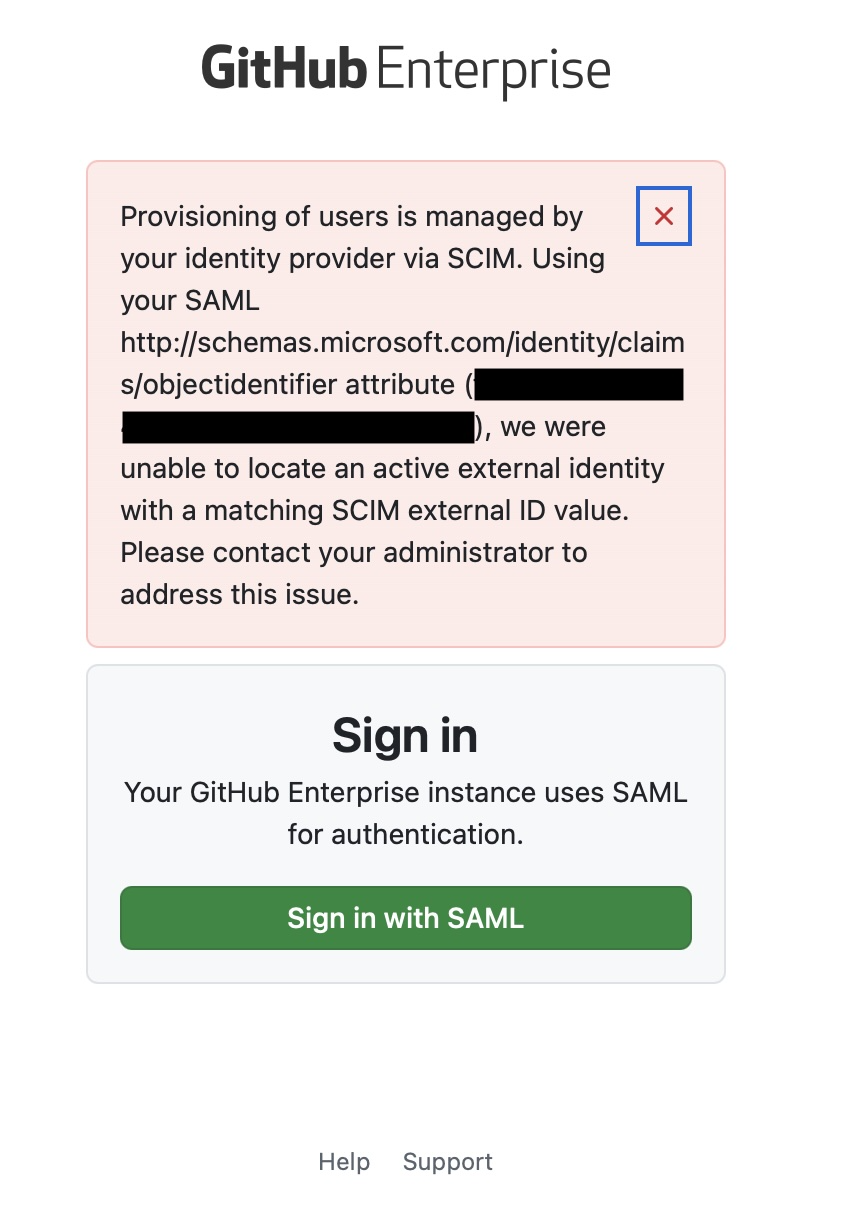
For all other identity providers, the error will look like:
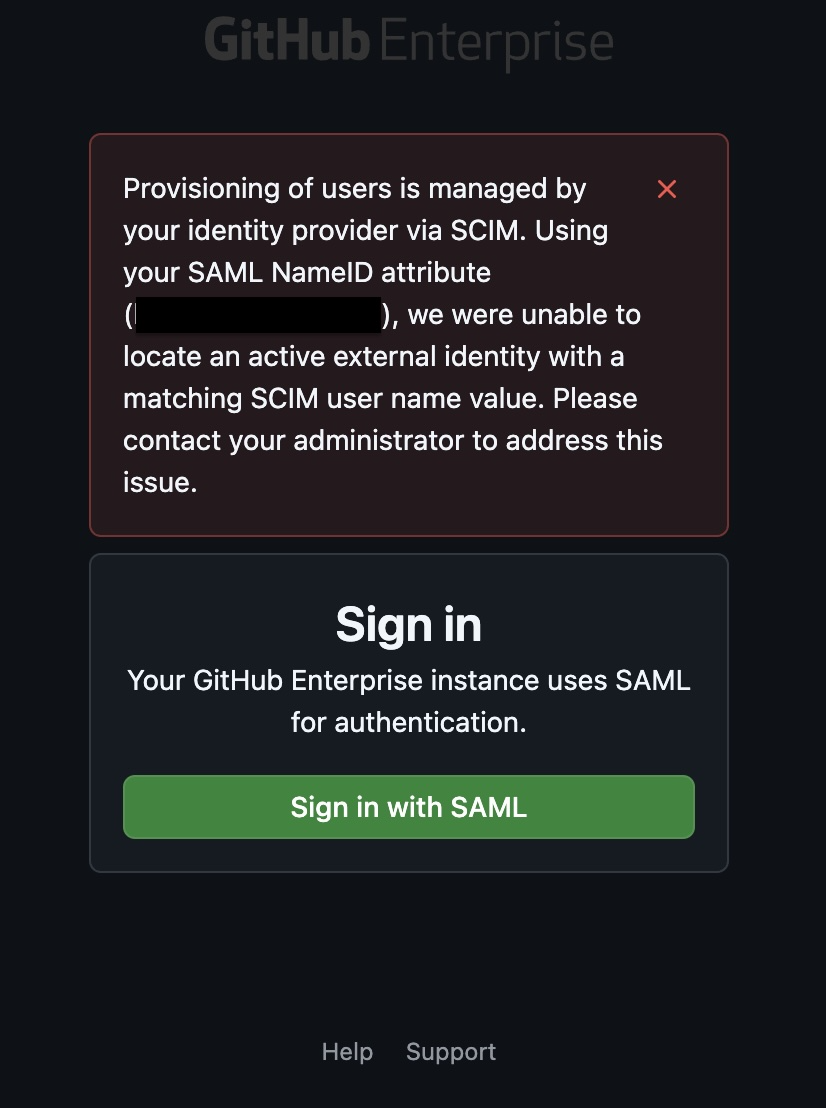
When this error occurs, please follow the steps below:
- Ensure that a SCIM identity has been provisioned for the user by searching through the users on your instance. For more information on how to find SCIM provisioned users on your instance, please see Viewing people in your enterprise.
- If the user has not been provisioned yet, it is either because the identity provider has not yet sent a provisioning request, or the provisioning request failed. Enterprise administrators can use their audit log events to determine which of these two scenarios they are impacted by. For more information, please see Provisioning users and groups with SCIM using the REST API.
- If the user has been successfully provisioned on your instance, you will need to ensure that the value for the SAML attribute listed in the error message matches the value of the listed SCIM attribute. To find the value for the SCIM attribute, please see Viewing and managing a user's SAML access to your enterprise.
- For example, to troubleshoot the screenshot above, we would look at the user's SCIM "External ID" value. Using that value, we would ensure that the user has the correct value set with the Identity Provider.
For more information on how GitHub maps SAML and SCIM data for users, please see REST API endpoints for SCIM.